Documentos de Académico
Documentos de Profesional
Documentos de Cultura
Two-Minute Drill - OCA
Cargado por
RafaelDerechos de autor
Formatos disponibles
Compartir este documento
Compartir o incrustar documentos
¿Le pareció útil este documento?
¿Este contenido es inapropiado?
Denunciar este documentoCopyright:
Formatos disponibles
Two-Minute Drill - OCA
Cargado por
RafaelCopyright:
Formatos disponibles
TWO-MINUTE DRILL
1.1 Position the Oracle Product Family
- The Oracle database stores and manages access to user data
- The Oracle Applications Server runs applications that connect users to the database
- Oracle Enterprise Manager is a tool for managing databases, application servers, and if desired, the entire computing environment
1.2 Explain Relational Structures
- Data must be normalized into two-dimensional tables
- Tables are linked through primary and foreign keys
- Entity-relationship diagrams represent the tables graphically
1.3 Understand the SQL Language
- SQL is a set-oriented language
- The DML command are: SELECT, INSERT, UPDATE, DELETE, and MERGE
- The DDL commands are: CREATE, ALTER, DROP, RENAME, TRUNCATE and COMMENT
- The DCL commands are: GRANT and REVOKE
- The TCL command are: COMMIT, ROLLBACK and SAVEPOINT
1.4 Appreciate the DBA's Role
- Sizing applications and server hardware
- Oracle software installation and maintenance
- Database physical design
- Monitoring and tuning performance
- Assisting developers with application design and tuning SQL
- Liaising with vendors, end users, developers, senior management, and other support groups
- Backup, restore and recovery
- User and security management
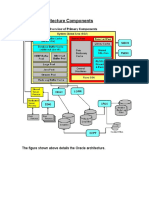
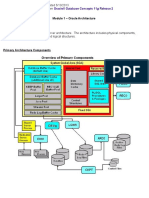
2.1 Describe the Single-Instance Architecture
- An Oracle server is an instance connected to a database
- An instance is a block of shared memory and a set of background processes
- A database is a set of files on disk
- A user session is a user process connected to a server process
2.2 Explain the Memory Structures
- The instance shared memory is the system global area (SGA)
- A session's private memory is its program global area (PGA)
- The SGA consists of a number of substructures, some of which are required (database buffer cache, log buffer, shared pool) and some of which
are optional (large pool, Java pool, Streams pool)
- The SGA structures can be dynamically resized and automatically managed, with the exception of the log buffer
2.3 Describe the Process Structures
- Session server processes are launched on demand when users connect
- Background server processes are launched at instance startup and persist until shutdown
- Server processes read from the database and background processes write to the database
- Some background processes will always be present (SMON, PMON, DBWn, LGWR, CKPT, MMON), while others will run depending on
what options have been enabled
2.4 Summarize the Storage Structures
- There are three required file types if a database: he controlfile, the online redo log files, and the datafiles
- The controlfile stores integrity information and pointers to the rest of the database
- The online redo logs store recent change vectors applied to the database
- External files include the parameter file, the password file, archive redo logs, and the log and trace files
- Logical data storage (segments), is abstracted from physical data storage (datafiles) by tablespaces
- A tablespace can consist of multiple datafiles
- Segments consist of multiple extents, which consist of multiple Oracle blocks, which consist of multiple operating system blocks
- A segment can have extents in several datafiles
3.1 Identify the Tools for Administering an Oracle Database:
- Installation: the OUI
- Database creation and upgrade: DBCA, DBUA
- For issuing ad hoc SQL: SQL*Plus, SQL Developer
- Backup: RMAN, Oracle Secure Backup
- Network administration: Oracle Net Manager, Oracle Net Configuration Assistant
- Data load and unload utilities: Datapump, SQL*Loader
- Management: Oracle Enterprise Manager, Database Control, Grid Control
3.2 Plan an Oracle Database Installation:
- Hardware requirements:
- Disk Space
- Main memory
- Swap space
- Temporary space
- Graphics terminal
- Operating system requirements:
- Certified version
- Necessary packages
- Kernel settings
OFA: an appropriate directory for the Oracle Base
3.3 Install the Oracle Software by Using the Oracle Universal Installer (OUI):
- Use a suitable operating system account
- Set necessary environment variables (Linux, Unix)
- Provide access to the root account (Linux, Unix)
- Make either an interactive or silent install
4.1 Create a Database by Using the Database Configuration Assistant:
- A database can be created with DBCA or from the SQL*Plus command line
- The DBCA can create a database from nothing or from a saved template
- The DBCA and SQL*Plus can delete a database
- An instance must be created before the database can be created
- Any options not selected at creation time can be added later
5.1 Describe the Stages of Database Startup and Shutdown:
- The stages are NOMOUNT, MOUNT, OPEN
- NOMOUNT mode requires a parameter file
- MOUNT mode requires the controlfile
- OPEN mode requires the datafiles and online redo log files
5.2 Set Database Initialization Parameters
- Static parameters cannot be changed without a shutdown/startup
- Other parameters can be changed dynamically, for the instance or a session
- Parameters can be seen in the dynamic performance views V$PARAMETER and V$SPPARAMETER
5.3 Use the Alert Log and Trace Files
- The alert log is a continuous stream of messages regarding critical operations
- Trace files are generated by background processes, usually when they hit errors
5.4 Use Data Dictionary and Dynamic Performance Views
- The dynamic performance views are populated from the instance or the controlfile
- The data dictionary views are populated from the data dictionary
- Dynamic performance views accumulate values through the lifetime of the instance, and are reinitialized at startup
- Data dictionary views show information that persists across shutdown and startup
- Both the data dictionary views and the dynamic performance views are published through synonyms
6.1 Configure and Manage the Oracle Network
- The server-side files are the listener.ora and (optionally) sqlnet.ora files
- The client-side files are the tnsnames.ora and (optionally) sqlnet.ora files
- The Oracle Net files are in ORACLE_HOME/network/admin, or in whatever directory the TNS_ADMIN variable points to
- Name resolution can be local (with tnsnames.ora file) or central (with a LDAP directory)
- Easy Connect does not need any name resolution
- One listener can listen for many databases
- Many listeners can connect to one database
- Instance registration with listeners can be static (by coding details in the listener.ora file) or dynamic (by the PMON process updating the
listener)
- Each user process has a persistent connection to its dedicated server process
6.2 Use the Oracle Shared Server Architecture
- User processes connect to dispatchers; these connections are persistent
- All dispatchers place requests on a common queue
- Shared server processes dequeue requests from the common queue
- Each dispatcher has its own response queue
- Shared server processes place results onto the appropriate dispatcher's response queue
- The dispatchers fetch results back to the appropriate user process
- Shared server is configured with (as a minimum) two instance parameters: DISPATCHERS and SHARED_SERVERS
7.1 Understand Tablespaces and Datafiles
- One tablespace can be many datafiles
- One tablespace can have many segments
- One segment is one or more extents
- One extent is many consecutive blocks, in one datafiles
- One Oracle block should be one or more operating system blocks
- The Oracle block is the granularity of database I/OFA
7.2 Create and Manage Tablespaces
- SMALLFILE tablespace can have many datafiles, but BIGFILE tablespace can have only one
- Tablespaces default to local extent management, automatic segment space management, but not to a uniform extent size
- OMF datafiles are automatically named, initially 100MB, and can autoextend without limit
- A tablespace that contains segments cannot be dropped, unless an INCLUDING DATAFILES clause is specified.
- Tablespaces can be online or offline, read-write or read-only
- Tablespaces can store three types of objects: permanent objects, temporary objects and undo segments.
7.3 Manage Space in Tablespaces
- Local extent management tracks extent allocation with bitmaps in each datafiles
- The UNIFORM SIZE clause when creating a tablespace forces all extents to be the same size
- The AUTOALLOCATE clause lets Oracle determine the next extent size, which is based on how many extents are being allocated to a segment
- Automatic segment space management tracks the free space in each block of an extent using bitmaps
- It is possible to convert a tablespace from dictionary extent management to local extent management, but not from freelist segment
management to automatic management
8.1 Create and Manage Database User Accounts
- User connects to a user account, which is connected to a schema
- All users must be authenticated before they can connect
- A user must have a quota on a tablespace before it can create any objects
- A user who owns objects cannot be dropped, unless the CASCADE keyword is used
8.2 Grant and Revoke Privileges
- By default, a user can do nothing. It cant even log on
- Direct privileges are always enabled
- A revocation of a system privilege dos not cascade; a revocation of an object privilege does
8.3 Create and Manage Roles
- Roles are no schema objects
- Roles can contain both system and object privileges, and other roles
- A role can be enabled or disabled for a session
8.4 Create and Manage Profiles
- Profiles can manage passwords and resource limits
- Password limits are always enforced; resource limits are dependent on an instance parameter
- Every user has a profile, by default the DEFAULT profile
9.1 Create and Modify Tables
- Tables are schema objects, sharing a namespace with views and synonyms
- After creation, column definitions can be added, dropped, or modified
9.2 Manage Constraints
- Constraints can be defined at table creation time, or added later
- A primary key is functionally equivalent to unique plus not null
- A unique constraint does not stop insertion of many null values
- Foreign key constraints define the relationships between tables
9.3 Create Indexes
- Indexes are required for enforcing unique and primary constraints
- NULLs are not included in B*Tree indexes but are included in bitmap indexes
- B*Tree indexes can be unique or non-unique, which determines whether they can accept duplicate key values
- B*Tree indexes are suitable for high cardinality columns, bitmap indexes for low cardinality columns
- Bitmap indexes can be compound, function based, or descending; B*Tree can also be unique, compressed, and reverse key.
9.4 Create and Use Temporary Tables:
- Rows in a temporary table are visible only to the session that inserted them
- DML on temporary tables does not generate redo
- Temporary tables exist only in session's PGA or in temporary segments
- A temporary table can keep rows for the duration of a session or a transaction, depending on how it was created
10.1 Manage Data Using DML
- All DML commands generate undo and redo
- Redo protects all changes to segments - undo segments, as well as data segments
- Server processes read from datafiles; DBWn writes to datafiles
10.2 Identify and Administer PL/SQL Objects
- Anonymous PL/SQL is stored on the client, stored PL/SQL in the data dictionary
- Procedures and functions can be packaged; triggers cannot be packaged
- PL/SQL code can call SQL code
10.3 Monitor and Resolve Locking Conflicts
- The default level of locking is row level
- Locks are required for all DML commands and are optional for SELECT
- A DML statement requires shared locks on the objects involved and exclusive locks on the rows involved
- A DDL locks requires an exclusive lock on the object it affects
- Deadlocks are resolved automatically
11.1 Explain the Purpose of Undo
- All DML statements generate undo data
- Undo data is used for transaction rollback and isolation and to provide read consistency, and also for flashback queries
- Automatic undo management using undo segments is the default with release 11g
11.2 Understand How Transactions Generate Undo
- Undo data will always be kept until the transaction that generated it completes with a COMMIT or a ROLLBACK. This is active undo.
- Undo data will be retained for a period after it become inactive to satisfy any read consistency requirements of long running queries. This is
unexpired undo.
- Undo data that is no longer needed for read consistency and may be overwritten at any time as space in undo segments is reused. This is
expired undo.
11.3 Manage Undo
- An instance will use undo segments in one nominated undo tablespace
- More undo tablespaces may exist, but only one will be used at a time
- The undo tablespace should be large enough to take into account the maximum rate of undo generation and the longest running query
- Undo tablespace datafiles are datafiles like any others
12.1 Database Security and Principle of Least Privilege
- Everything not specifically permitted should be forbidden
- The DBA and the system administrator should not be the same person
- Privileges granted to the PUBLIC role must be monitored
- Security-critical instance parameters must be monitors and cannot be changed without restarting the instance
12.2 Work with Standard Database Auditing
- Database auditing can be oriented towards privileges, commands, or objects
- Audit records can be directed toward a database table or the operating system
- Database audit records are stored in the SYS>AUD$ data dictionary table
- FGA can be directed toward particular rows and columns
- Auditing can also be implemented with database triggers
13.1 Use and Manage Optimizer Statistics
- Object statistics are gathered automatically, unless STATISTICS_LEVEL is BASIC
- Object statistics are not maintained in real time
- The AWR stores a history of object statistics; the current statistics are stored in the data dictionary
13.2 Use and Manage the Automatic Workload Repository
- By default, snapshots are taken every hour and stored for eight days
- Additional snapshots can be taken on demand
- Snapshots can be preserved indefinitely if nominated for a baseline
- MMON is responsible for creating snapshots and launching the ADDM
- The AWR consists of tables (and related objects) in the SYSMAN schema, in the SYSAUX tablespace
13.3 Use the Advisory Framework
- The ADDM runs automatically whenever a snapshot os taken, and manually on demand
- ADDM reports will give advice directly and may recommend running other advisors
- By default, the SQL Tuning Advisor and the Segment Advisor will run automatically in the maintenance windows
- Setting STATISTICS_LEVEL to BASIC will disable gathering snapshots and running the advisors
13.4 Manage Alerts and Thresholds
- Stateful alerts must be configured with thresholds
- If a stateful alert is raised, it will remain until the situation is cleared; stateless reports are reported and do not need to be cleared
- Thresholds are stored in the AWR
- It is the MMON background process that raises an alert, and (usually) Enterprise Manager that reports it
14.1 Use Automatic Memory Management
- Automatic Shared Memory Management can be enabled with the parameter SGA_TARGET
- Automatic PGA Management can be enabled with the parameter PGA_AGGREGATE_TARGET
- Automatic Memory Management can be enabled with the parameter MEMORY_TARGET
14.2 Use Memory Advisor
- There are advisors for PGA, SGA, and total memory usage
- The advisors can be accessed by querying dynamic performance views, or through Enterprise Manager
14.3 Troubleshoot Invalid and Unusable Objects
- Procedural objects will become invalid if the object on which they depend are changed
- Indexes will become unusable if their table is moved
- Oracle will attempt to recompile invalid procedural object automatically
- Unusable indexes must be rebuilt manually
- Oracle will not attempt to use an unusable index, so there will be no errors
15.1 Identify Types of Failure That can Occur in an Oracle Database
- Instance failure results in automatic instance recovery on the next startup
- Session failures are managed automatically by the PMON process
- User errors can be reversed using a number of techniques
- Recovering from media failures requires use of backups and archive logs
15.2 Describe Ways to Tune Instance Recovery
- Instance recovery is automatic and unstoppable
- Instance recovery applies change vectors from the online redo log files, since the last incremental checkpoint position
- The time taken for instance recovery is dependent on the amount of redo to be applied, and the number of I/O on datafiles needed to apply it.
- The FAST_START_MTTR_TARGET parameter sets a maximum time for recovery, using a self-tuning mechanism
- If FAST_START_MTTR_TARGET is set, it will also enable the checkpoint auto-tuning process to reduce recovery time further
15.3 Identify the Importance of Checkpoints, Redo Log Files, and Archived Log Files
- Full checkpoints occur only on orderly shutdown or on demand
- Partial checkpoints occur automatically when necessary
- Incremental checkpoints advance the point in the redo stream from which recovery must begin after an instance failure
- The redo log consists of the disk structures for storing change vector. The online log is essential for instance recovery
- The archive log consists of copies of online log file members, created as they are files. These are essential for datafile recovery after media
failure
15.4 Overview of Flash Recovery Area
- The flash recovery area is configured with the instance parameters DB_RECOVERY_FILE_DEST and DB_RECOVERY_FILE_DEST_SIZE
- The flash recovery area is a default destination fir all recovery-related files
15.5 Configure ARCHIVELOG Mode
- In archivelog mode, an online log file member cannot be overwritten until it has been archived
- Archive processes start automatically when archivelog mode is enabled
- The mode can only be changed when the database is mounted
16.1 Create Consistent Database Backups
- A consistent backup is one made after the database has been shut down
- A user-managed consistent backup has three steps: copy the online redo log files, copy the controlfiles, copy the datafiles
- A server-managed consistent backup has also three steps: mount the database, back up the controlfile, back up the datafiles
- RMAN will never back up online log files or tempfiles
16.2 Back up your Database Without Shutting It Down
- A user-managed open backup has three steps: archive the online redo log files, ALTER DATABASE BACKUP CONTROLFILE TO..., copy
the datafiles, while their tablespace is in backup mode
- A server-managed open backup has also three steps: archive online redo log files, back up the controlfile, back up the datafiles, without the
need to enable backup mode
16.3 Create Incremental Backups
- User-managed backups cannot be incremental, but server-managed backups can be
- The starting point for an incremental strategy must be an incremental level 0 backup. A full backup cannot be used
- The incremental levels are 0, 1, or cumulative
- Incremental backups can be made in archivelog or noarchivelog mode
16.4 Automate Database Backups
- User- or server-managed backup jobs can be scheduled with the operating system scheduler
- The Enterprise Manager job system can schedule server-managed backups of all types
16.5 Manage Backups, View Backup Reports, and Monitor the Flash Recovery Area
- Server-managed backups are recorded in a repository, in the target database's controlfile
- The repository can be checked with reality with the CROSSCHECK command, and modified if necessary
- User-managed backups can be recorded in the repository and thus brought under RMAN control by using the CATALOG command
- If backing up to the flash recovery area, its usage must be monitored
17.1 Overview of Data Recovery Advisor
- The ADR is a set of files in the DIAGNOSTIC_DEST directory
- The DRA can repair damage to datafiles and controlfile, and replace missing log file groups
- Restore and recovery of the controlfile or a critical datafile can be done only in mount mode
- Restore and recovery of a non-critical datafile can be done while the database is open
17.2 Use Dara Recovery Advisor to Perform Recovery (Controlfile, Redo Log file, and Datafile)
- Failures must be listed before they can be advised upon
- The DRA can be accessed through the RMAN executable or with Enterprise Manager
- The DRA is available in all modes: in nomount mode it can repair the controlfile, in mount mode or open mode it can repair datafiles
18.1 Describe and Use Methods to Move Data (Directory Objects, SQL*Loader, External Tables)
- Directory objects map an Oracle directory to an operating system directory
- Directory objects are owned by SYS, and read or write permissions can be granted to users
- SQL*Loader is a client-server tool that works over normal database sessions
- SQL*Loader control file read a wide variety of formats, if configures correctly
- External tables in the ORACLE_LOADER format can be queries from within the database as though they were normal heap tables
- It is not possible to perform DML on external tables, but they can be created and populated by Data Pump using CREATE TABLE... AS
SELECT...
18.2 Explain the General Architecture of Oracle Data Pump
- Data Pump uses server-side processes; the client tools manage jobs, they do not execute them
- Data Pump will always use direct path, unless the complexity of the objects precludes this
18.3 Use Data Pump Export and Import to Move Data Between Oracle Databases
- A Data Pump dump file can only bee read by Data Pump
- The network mode of Data Pump copies data between databases without staging it on disk
- Data Pump always reads and writes Oracle directories; it is not aware of the operating system directory structure
19.1 Use the Enterprise Manager Support Workbench
- Database Control can connect to MetaLink and identify lists of advised patches
- The Support Workbench can classify errors into named problems, each consisting of one or more incidents
- Diagnostic information is stored on files in the ADR, located by default in the ORACLE_BASE
- All diagnostic information in the ADR relevant to a problem can be packaged for transmission to Oracle Support Services
19.2 Manage Patches
- Interim patches fix one problem
- CPUs are bundled patches, often including security fixes
- Patch sets raise the level of the product
- The Opatch utility installs patches, and updates the inventory
También podría gustarte
- Starting Database Administration: Oracle DBADe EverandStarting Database Administration: Oracle DBACalificación: 3 de 5 estrellas3/5 (2)
- Introduction to Oracle Database AdministrationDe EverandIntroduction to Oracle Database AdministrationCalificación: 5 de 5 estrellas5/5 (1)
- Oracle Database Security: Presented by Wilson CriderDocumento94 páginasOracle Database Security: Presented by Wilson Cridersaravanand1983Aún no hay calificaciones
- Module 1 - Oracle Architecture: ObjectivesDocumento41 páginasModule 1 - Oracle Architecture: ObjectivesNavneet SainiAún no hay calificaciones
- Module 1 - Oracle ArchitectureDocumento34 páginasModule 1 - Oracle ArchitecturePratik Gandhi100% (1)
- Database Architecture Oracle DbaDocumento41 páginasDatabase Architecture Oracle DbaImran ShaikhAún no hay calificaciones
- 3 Oracle Architecture NotesDocumento39 páginas3 Oracle Architecture NotesPaul NikolaidisAún no hay calificaciones
- Oracle DBA ArchitectureDocumento17 páginasOracle DBA ArchitectureDiwakar Reddy SAún no hay calificaciones
- Module 1 - Oracle ArchitectureDocumento33 páginasModule 1 - Oracle ArchitectureDivya SrinivasanAún no hay calificaciones
- Module 1 - Oracle ArchitectureDocumento110 páginasModule 1 - Oracle ArchitectureKranthi KumarAún no hay calificaciones
- Dbai Les01 Rev1 1Documento56 páginasDbai Les01 Rev1 1primeroseAún no hay calificaciones
- Module 1 - Oracle Architecture: ObjectivesDocumento64 páginasModule 1 - Oracle Architecture: Objectivesshaikali1980Aún no hay calificaciones
- Describe Oracle Architecture in Brief.: AnswerDocumento8 páginasDescribe Oracle Architecture in Brief.: AnswersonijayminAún no hay calificaciones
- Module 1 - Oracle ArchitectureDocumento34 páginasModule 1 - Oracle ArchitectureGautam TrivediAún no hay calificaciones
- Oracle Database Architecture OverviewDocumento24 páginasOracle Database Architecture OverviewSuneel KumarAún no hay calificaciones
- oRACLE NotesDocumento15 páginasoRACLE NotesCarla MissionaAún no hay calificaciones
- Presentation Lesson1Documento19 páginasPresentation Lesson1Troy Lenner ParedesAún no hay calificaciones
- Exploring Oracle Database ArchitectureDocumento15 páginasExploring Oracle Database ArchitectureElliott MadimabeAún no hay calificaciones
- Object Oriented - Interview Questions: What Is OOP?Documento18 páginasObject Oriented - Interview Questions: What Is OOP?Sam RogerAún no hay calificaciones
- Oracle BasicsDocumento30 páginasOracle BasicsRaghunath Reddy100% (1)
- A Summer Training Presentation On Oracle 10G andDocumento24 páginasA Summer Training Presentation On Oracle 10G andPiyush JainAún no hay calificaciones
- Exploring The Oracle Database ArchitectureDocumento28 páginasExploring The Oracle Database ArchitectureAneesh TiggaAún no hay calificaciones
- Parameter? - COST and RULEDocumento3 páginasParameter? - COST and RULEraajiAún no hay calificaciones
- DBADocumento112 páginasDBATejas DixitAún no hay calificaciones
- Case Study-Oracle Mod IiiDocumento63 páginasCase Study-Oracle Mod IiiNevin FrancisAún no hay calificaciones
- Starting up and shutting down Oracle database instancesDocumento9 páginasStarting up and shutting down Oracle database instancesambica badanaAún no hay calificaciones
- Introduction of Oracle-1Documento62 páginasIntroduction of Oracle-1hiwot kebedeAún no hay calificaciones
- SQL QuestionsDocumento5 páginasSQL Questionsadil5821020Aún no hay calificaciones
- Oracle Architechture & ConceptsDocumento90 páginasOracle Architechture & ConceptsElango GopalAún no hay calificaciones
- Summary OracleDocumento39 páginasSummary OracleRoel DonkerAún no hay calificaciones
- Oracle SM IDocumento388 páginasOracle SM ITanmoy NandyAún no hay calificaciones
- Chapter - 1: Oracle Architecture - Module 1Documento39 páginasChapter - 1: Oracle Architecture - Module 1Vivek MeenaAún no hay calificaciones
- SQL LectureDocumento23 páginasSQL LectureJai PrakashAún no hay calificaciones
- ORACLE ClassDocumento26 páginasORACLE Classssv pAún no hay calificaciones
- Database Creation Pre-RequsitesDocumento37 páginasDatabase Creation Pre-RequsitesskarumajAún no hay calificaciones
- Oracle Database Administration Hand BookDocumento78 páginasOracle Database Administration Hand Bookmarioy4783% (12)
- Oracle PL/SQL FundamentalsDocumento26 páginasOracle PL/SQL FundamentalsChaitu BachuAún no hay calificaciones
- CSE 8th Sem DBADocumento119 páginasCSE 8th Sem DBAvidhi hinguAún no hay calificaciones
- SQL Tuning 11g CustomizedDocumento873 páginasSQL Tuning 11g CustomizedMamataMaharanaAún no hay calificaciones
- Chapter 1. Oracle Database ArchitectureDocumento7 páginasChapter 1. Oracle Database ArchitectureAdryan AnghelAún no hay calificaciones
- ORACLE ArchitectureDocumento23 páginasORACLE Architecturechamod tharushaAún no hay calificaciones
- 08-System Databases in SQL Server 2005 PDFDocumento4 páginas08-System Databases in SQL Server 2005 PDFdivandannAún no hay calificaciones
- Oracle-9: Unit - 9 (A) One Mark QuestionsDocumento12 páginasOracle-9: Unit - 9 (A) One Mark QuestionsJonty BabaAún no hay calificaciones
- 3 Managing DatabaseDocumento63 páginas3 Managing DatabaseKireina HidayatAún no hay calificaciones
- Oracle Dba NotesDocumento20 páginasOracle Dba Notessash_8Aún no hay calificaciones
- Data Gaurd 10 GsheetDocumento10 páginasData Gaurd 10 GsheetJonJonAún no hay calificaciones
- DBA Course OutlineDocumento8 páginasDBA Course OutlinePandarinath TssmAún no hay calificaciones
- Technical Skills Enhancement - PL/SQL Best Practices Oracle ArchitectureDocumento35 páginasTechnical Skills Enhancement - PL/SQL Best Practices Oracle ArchitectureHuynh Sy NguyenAún no hay calificaciones
- Database Architecture and ASMDocumento41 páginasDatabase Architecture and ASMPradpm KumAún no hay calificaciones
- Database NotesDocumento31 páginasDatabase NotesSaad QaisarAún no hay calificaciones
- Introduction To CMIS 565 - Module 0Documento9 páginasIntroduction To CMIS 565 - Module 0kamakom78Aún no hay calificaciones
- Oracle10g Introduction1eryk 130405011929 Phpapp02Documento34 páginasOracle10g Introduction1eryk 130405011929 Phpapp02Sonali SinghAún no hay calificaciones
- Basics of The Oracle Database ArchitectureDocumento56 páginasBasics of The Oracle Database Architecturevidhi hinguAún no hay calificaciones
- Oracle ArchDocumento3 páginasOracle ArchMansi TanejaAún no hay calificaciones
- Less01 DBA1Documento34 páginasLess01 DBA1Percy Joel Gómez MamaniAún no hay calificaciones
- Database Architecture: - Mysql Architecture - Oracle Architecture - SQL Server ArchitectureDocumento10 páginasDatabase Architecture: - Mysql Architecture - Oracle Architecture - SQL Server ArchitectureDo Van TuAún no hay calificaciones
- Using Ola Hallengrens SQL Maintenance Scripts PDFDocumento28 páginasUsing Ola Hallengrens SQL Maintenance Scripts PDFHana IbisevicAún no hay calificaciones
- PIA Training Centre Prime CommunicationsDocumento14 páginasPIA Training Centre Prime CommunicationsArbabAún no hay calificaciones
- Concise Oracle Database For People Who Has No TimeDe EverandConcise Oracle Database For People Who Has No TimeAún no hay calificaciones
- Interview Question For Oracle DBADocumento111 páginasInterview Question For Oracle DBAVimlendu Kumar100% (1)
- Saa SDocumento1 páginaSaa SRafaelAún no hay calificaciones
- AoT Initiative Evaluation CriteriaDocumento1 páginaAoT Initiative Evaluation CriteriaRafaelAún no hay calificaciones
- SaaS 2022Documento2 páginasSaaS 2022RafaelAún no hay calificaciones
- 2013-Db-Oded Raz-Implementing Oracle Database Vault - Step by Step-ManuskriptDocumento5 páginas2013-Db-Oded Raz-Implementing Oracle Database Vault - Step by Step-ManuskriptRafaelAún no hay calificaciones
- 1z0-060 v2015-03-01 by EMMIE 150qDocumento117 páginas1z0-060 v2015-03-01 by EMMIE 150qaramis01Aún no hay calificaciones
- Aindumps.1z0 060.v2017!05!03.by - Ramanathan v.129qDocumento102 páginasAindumps.1z0 060.v2017!05!03.by - Ramanathan v.129qRafaelAún no hay calificaciones
- Oracle PrivilegesDocumento7 páginasOracle PrivilegesRafaelAún no hay calificaciones
- 1z0-060 v2015-04-01 by Cleveland 131qDocumento108 páginas1z0-060 v2015-04-01 by Cleveland 131qaramis01Aún no hay calificaciones
- Oracle ActualTests 1z0-068 v2016-09-07 by Xsan 77q PDFDocumento57 páginasOracle ActualTests 1z0-068 v2016-09-07 by Xsan 77q PDFRafaelAún no hay calificaciones
- Oracle - Testinside.1z0 060.v2014!03!10.by - Watson.115qDocumento76 páginasOracle - Testinside.1z0 060.v2014!03!10.by - Watson.115qRafaelAún no hay calificaciones
- Oracle - Selftestengine.1z0 060.v2014!03!19.by - Ruth.67qDocumento47 páginasOracle - Selftestengine.1z0 060.v2014!03!19.by - Ruth.67qRafaelAún no hay calificaciones
- Oracle - Actualtests.1z0 060.v2015!03!28.by - Lucile.150qDocumento126 páginasOracle - Actualtests.1z0 060.v2015!03!28.by - Lucile.150qRafaelAún no hay calificaciones
- ORACLE DBA Activity ChecklistDocumento12 páginasORACLE DBA Activity ChecklistRafaelAún no hay calificaciones
- Interview Question For Oracle DBADocumento111 páginasInterview Question For Oracle DBAVimlendu Kumar100% (1)
- Oracle RolesDocumento14 páginasOracle RolesRafaelAún no hay calificaciones
- Oracle - Prep4sure.1z0 068.v2016!07!12.by - Lana.60qDocumento49 páginasOracle - Prep4sure.1z0 068.v2016!07!12.by - Lana.60qLuis AlfredoAún no hay calificaciones
- DBA ScriptsDocumento25 páginasDBA Scriptschavandilip100% (2)
- Oracle Certkey 1z0-060 v2014-03-13 by Judy 78qDocumento55 páginasOracle Certkey 1z0-060 v2014-03-13 by Judy 78qRafaelAún no hay calificaciones
- Oracle - Passit4sure.1z0 060.v2015!03!03.by - florENCE.150qDocumento117 páginasOracle - Passit4sure.1z0 060.v2015!03!03.by - florENCE.150qThangavelu AgathianAún no hay calificaciones
- 1z0-060 v2015-04-01 by Cleveland 131qDocumento108 páginas1z0-060 v2015-04-01 by Cleveland 131qaramis01Aún no hay calificaciones
- Oracle - Actualtests.1z0 060.v2015!04!03.by - Johnnie.108qDocumento92 páginasOracle - Actualtests.1z0 060.v2015!04!03.by - Johnnie.108qRafaelAún no hay calificaciones
- Asm 12c Powerful FrameworkDocumento18 páginasAsm 12c Powerful FrameworkRafaelAún no hay calificaciones
- Upgrade to Oracle Database 12c Exam 1z0-060Documento67 páginasUpgrade to Oracle Database 12c Exam 1z0-060RafaelAún no hay calificaciones
- 1Documento7 páginas1RafaelAún no hay calificaciones
- 2.8 Inch Palm & FP Terminal General Quick Start Guide - V1.0 - 20170512Documento18 páginas2.8 Inch Palm & FP Terminal General Quick Start Guide - V1.0 - 20170512Daniel BholahAún no hay calificaciones
- CV SYS Admin Curse-R02Documento242 páginasCV SYS Admin Curse-R02kibirAún no hay calificaciones
- imageRUNNER ADVANCE C9200 PRO C7200 Series SM Rev6 101716 PDFDocumento1864 páginasimageRUNNER ADVANCE C9200 PRO C7200 Series SM Rev6 101716 PDFLucasCardosoAún no hay calificaciones
- Net-Net Route Manager Central 1.0 User GuideDocumento98 páginasNet-Net Route Manager Central 1.0 User GuideMyoungHwan JeongAún no hay calificaciones
- Section 1. Example: Major Goals of A Disaster Recovery PlanDocumento10 páginasSection 1. Example: Major Goals of A Disaster Recovery PlanNadia Silviana100% (1)
- 3rd Chapter Notes ICT 0417Documento9 páginas3rd Chapter Notes ICT 0417FahimSiddiqAún no hay calificaciones
- Kaspersky Security Center test questionsDocumento13 páginasKaspersky Security Center test questionsMusa Al-DalouAún no hay calificaciones
- Auditing Theory Auditing in A Computer Information Systems (Cis) EnvironmentDocumento32 páginasAuditing Theory Auditing in A Computer Information Systems (Cis) EnvironmentMajoy BantocAún no hay calificaciones
- Chapter One Introduction To System Network AdministrationDocumento25 páginasChapter One Introduction To System Network AdministrationmeshAún no hay calificaciones
- BCV 3000073gDocumento27 páginasBCV 3000073gsunny shahAún no hay calificaciones
- 3 Om650Documento45 páginas3 Om650Raul CallejasAún no hay calificaciones
- Database Systems - Questions and Mark SchemesDocumento19 páginasDatabase Systems - Questions and Mark SchemesDavid Thomas100% (1)
- Active Directory TrainingDocumento124 páginasActive Directory Trainingflory_vladeanuAún no hay calificaciones
- Ax41-000 814 01 02 02Documento26 páginasAx41-000 814 01 02 02Bashir AhmedAún no hay calificaciones
- Datasheet PLC OMRON CP1EDocumento40 páginasDatasheet PLC OMRON CP1ETiar Kusuma Dewi100% (3)
- EDB Event 22062017 EDB Vs OracleDocumento63 páginasEDB Event 22062017 EDB Vs Oraclenandex777Aún no hay calificaciones
- Fortinet - Certkiller.FCNSA .V5.v2015-04-08.by .Florine.119qDocumento58 páginasFortinet - Certkiller.FCNSA .V5.v2015-04-08.by .Florine.119qSathish MAún no hay calificaciones
- Run Issue 42 1987 JunDocumento108 páginasRun Issue 42 1987 JunGeoffrey de VlugtAún no hay calificaciones
- What Are The Different Kinds of Backup?Documento7 páginasWhat Are The Different Kinds of Backup?Zaheer AbbasAún no hay calificaciones
- Css 4th Quarter ExamDocumento7 páginasCss 4th Quarter ExamLorenzo Moreno Jr.100% (3)
- CC Ques Bank Cloud Computing QB UNIT 5Documento7 páginasCC Ques Bank Cloud Computing QB UNIT 5aparna chinnarajAún no hay calificaciones
- 21 Secrets of FilemakerDocumento10 páginas21 Secrets of FilemakerSimon Dominguez ArangurenAún no hay calificaciones
- Free Torrent: Free and Valid Exam Torrent Helps You To Pass The Exam With High ScoreDocumento4 páginasFree Torrent: Free and Valid Exam Torrent Helps You To Pass The Exam With High Scorefrfa01Aún no hay calificaciones
- Optimizing SQL Server For Temenos T24Documento68 páginasOptimizing SQL Server For Temenos T24Indra Gunawan100% (1)
- IT General ControlsDocumento6 páginasIT General ControlsPatrick mdaganoAún no hay calificaciones
- CnMaestro On-Premises User Guide - 4.1.0Documento801 páginasCnMaestro On-Premises User Guide - 4.1.0Muzammil Okay OkayAún no hay calificaciones
- CyberSense For Dell PowerProtect Cyber Recovery 1656644381Documento12 páginasCyberSense For Dell PowerProtect Cyber Recovery 1656644381Marcelo MafraAún no hay calificaciones
- Veritas NetBackup Advanced AdministrationDocumento2 páginasVeritas NetBackup Advanced AdministrationcAún no hay calificaciones
- Helen Ross Mcnabb Case StudyDocumento5 páginasHelen Ross Mcnabb Case StudyIntegracon TechnologiesAún no hay calificaciones
- Ibrahim M Al Amshan: Ref: GC955-500Documento8 páginasIbrahim M Al Amshan: Ref: GC955-500iamshanAún no hay calificaciones